Information Management
 © UNICEF/NYHQ2004-0662/Kate Brooks
© UNICEF/NYHQ2004-0662/Kate Brooks
What is information management for MRM?
Information comes in many different forms and can be organized in different ways depending on the aims of the system and it can be managed using many different techniques and tools. Information management for MRM will vary in different countries and contexts but should cover the management of information from the time it is collected in the field, to recording that information in regular reports, through to analysis of the information and how this is presented and made accessible for specific reports, etc. The objective is to implement efficient, confidential and secure management of information that leads to sound analysis for reports and responses. This will ensure that the MRM operates efficiently and provides as accurate a picture as possible.
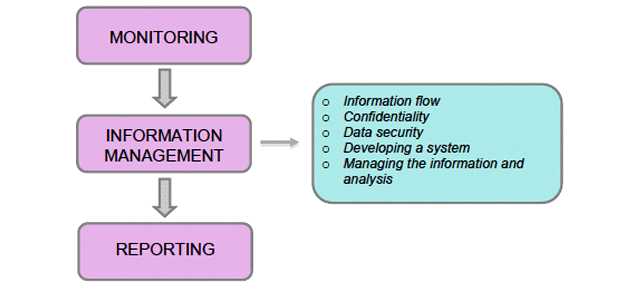
Figure 4: An overview of information management and its components
Flow of information
The following are some comments and questions to be taken into account for processing information. It is suggested that an agreed process is determined and clear written guidance provided on the specifics of who does what.
- When information has been collected in the field, clarify whom the field staff should provide the report to (designated information focal point). This will vary within different organizations but needs to be clearly outlined.
- Is a centralized information management system safe or necessary?
- Do field staff provide a hard copy report or electronic?
- How is information shared among organizations? That is, what information-sharing protocols are in place, if any?
- Identify one focal point in each field location for managing information if appropriate.
- How is information transferred from the field office to the central location?
- Who is responsible for ensuring information is recorded accurately? Who do the checks for accuracy in information input?
- Who is responsible for analysing and generating reports?
Confidentiality
The greatest area of concern for participating organizations and particularly NGOs has been in the aspect of confidentiality. The MRM can be secure and confidential, but certain parameters have to be agreed and clear guidance provided and adhered to. The information below provides some comments and poses questions that need consideration when establishing the MRM.
- What information is required? Does this need to be detailed with personal information or can this be anonymized? It is possible for the reporting agency (e.g., NGO) to hold the personal data but for anonymous information be provided for MRM data recording and analysis? (Does this work for application of MRM in your country?)
- When interviewing, confidentiality can only be assured if the interview is conducted in private. If others are listening, the staff member cannot assure confidentiality.
- If information is provided when in a group situation, inform the group that in such a setting you cannot assure confidentiality.
- Witness name and address may be recorded but should remain confidential. Names and addresses would only be used with consent (and this would be rare).
- No personal information to be shared with the government or other groups (except for where advocacy has been requested and consent provided. (See Responses.)
- Concern is not only for the victims but also for the monitoring staff and the organizations. This risk can be reduced by using codes or reference numbers in place of the names of monitoring staff and organizations (can also be used for victims/survivors and witnesses). A list cross-referencing the codes with the individual organization details can then be kept separately in another location.
Information security
- In certain circumstances, highly sensitive information may need to be subject to additional security precaution such as restrictive access, etc. Information that is not deemed highly sensitive should be accessible to a larger number of CTFMR partners. Security protocols should be worked out at the CTFMR level at an early stage.
- Information should be held in a secure location with named people as key holders or with access to passwords.
- All paper records require a lockable filing cabinet or cupboard available exclusively for this purpose.
- All electronic information must be protected. Field-level IT experts should be consulted at an early stage to assist the CTFMR.
- Design an emergency strategy. If you need to evacuate an office, how will the information be protected and how will confidentiality be preserved?